
MagicTree
Have you ever spent ages trying to find the results of a particular portscan you were sure you did? Or grepping through a bunch of files looking for data for a particular host or service? Or copy-pasting bits of output from a bunch of typescripts into a report? We certainly did, and that's why we wrote MagicTree - so that it does such mind-numbing stuff for us, while we spend our time hacking.
MagicTree is a penetration tester productivity tool. It is designed to allow easy and straightforward data consolidation, querying, external command execution and (yeah!) report generation. In case you wonder, "Tree" is because all the data is stored in a tree structure, and "Magic" is because it is designed to magically do the most cumbersome and boring part of penetration testing - data management and reporting.
Magictree capabilities
Running Nmap
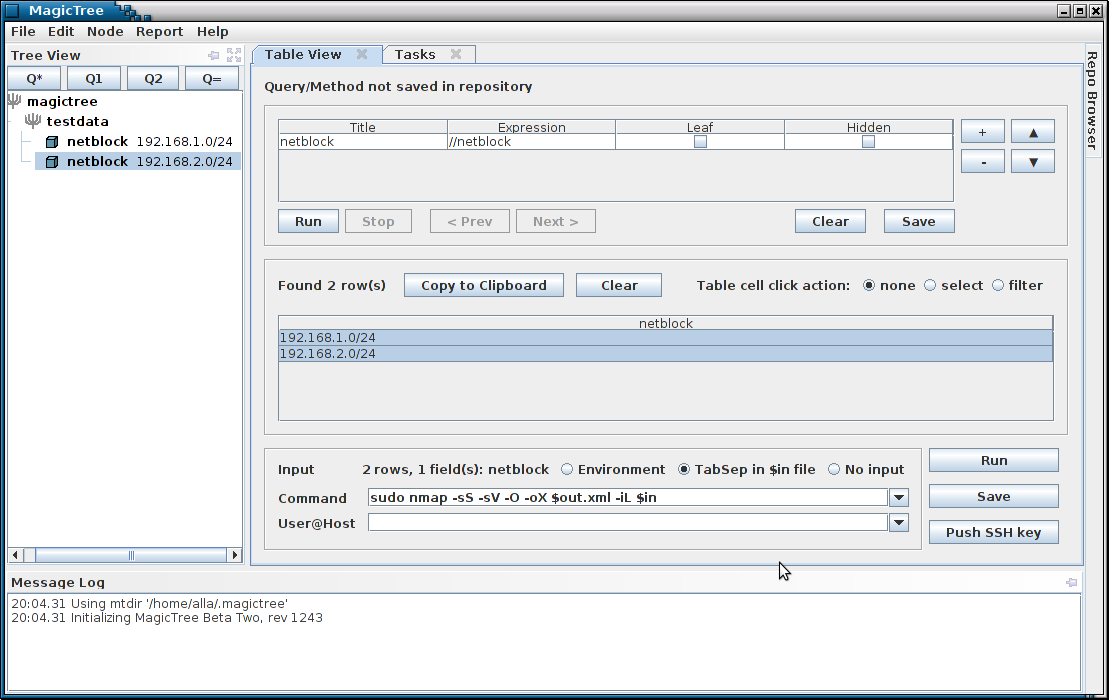
Importing Nmap Data
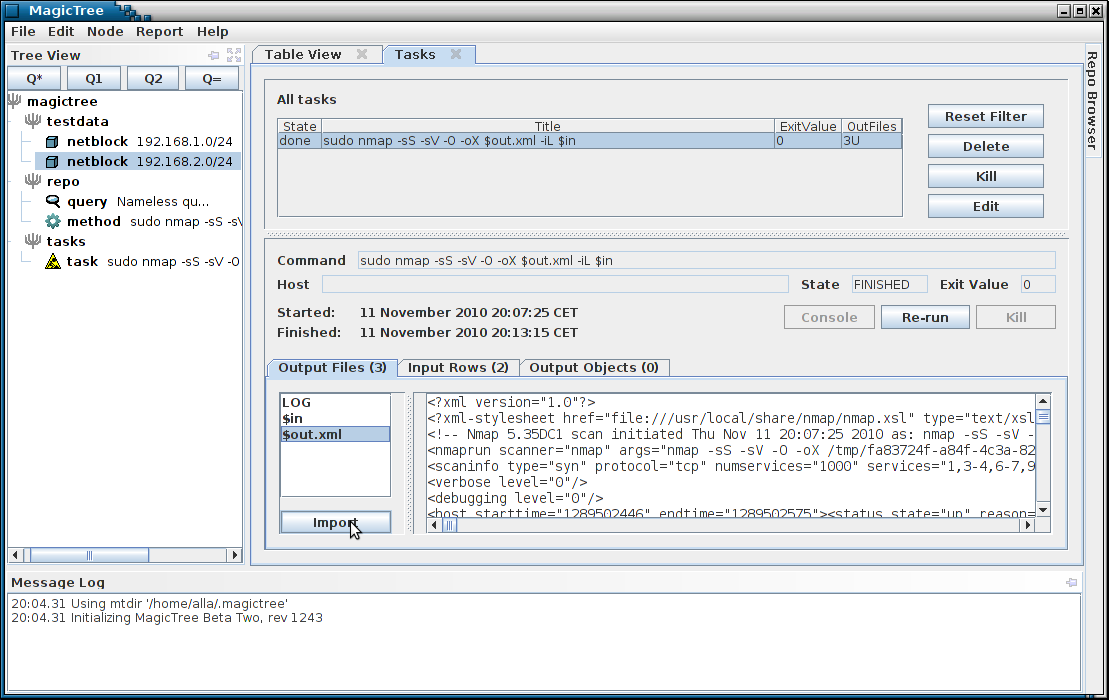
Querying Nmap Data
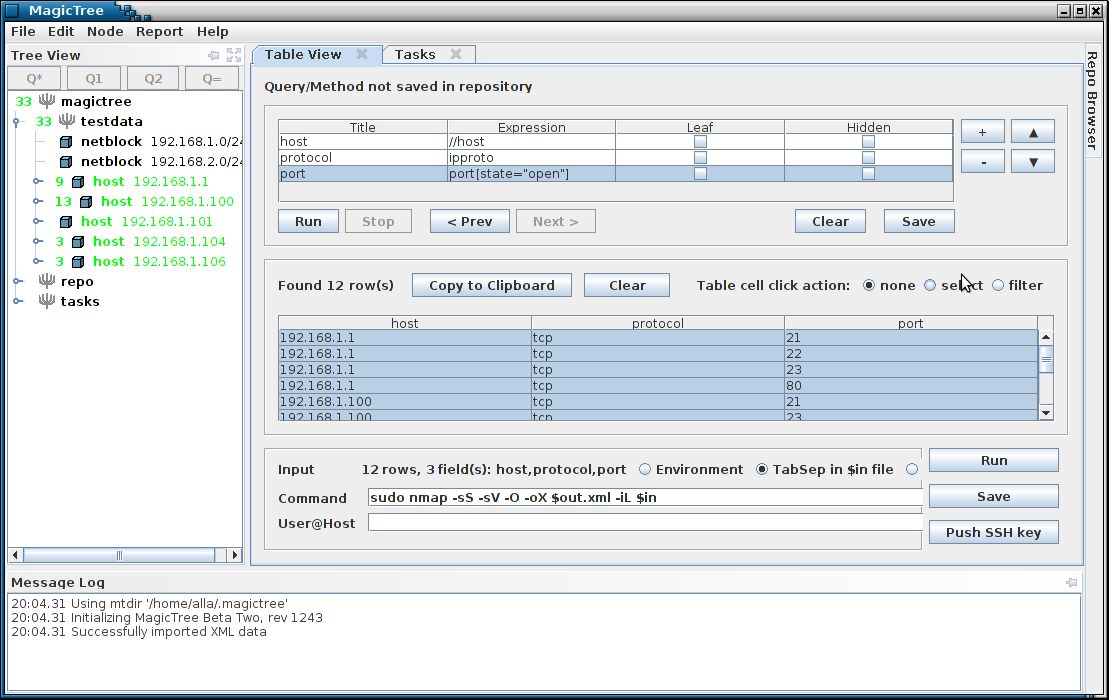
Importing Nessus Data
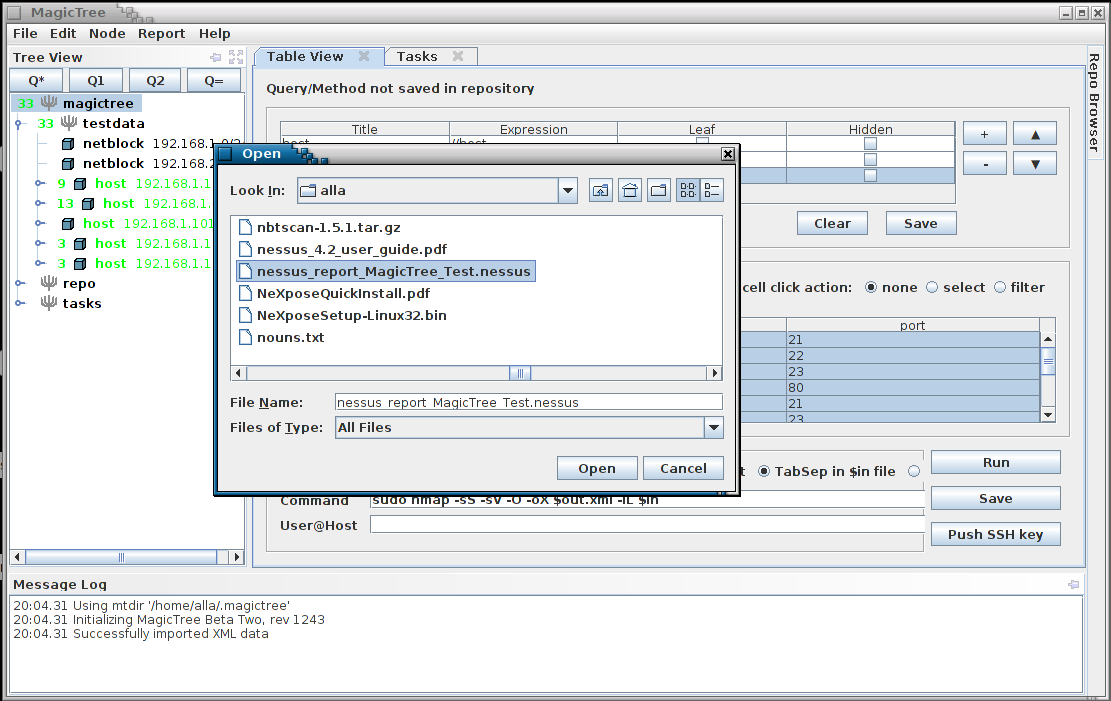
Listing Findings By Severity
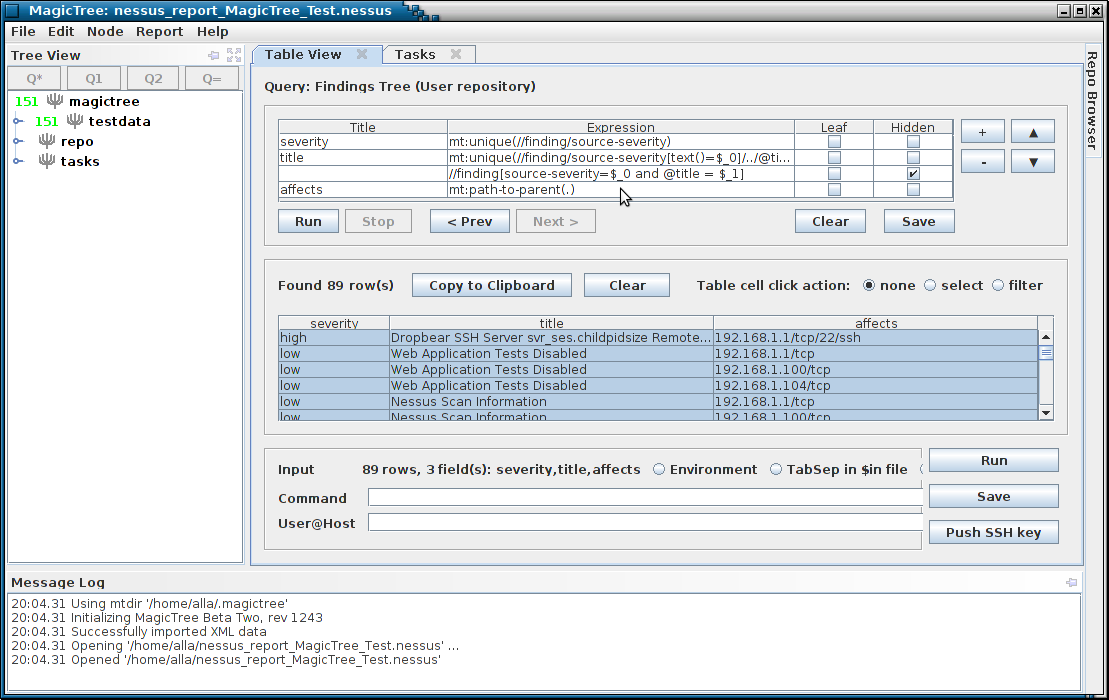
Magictree Report Template
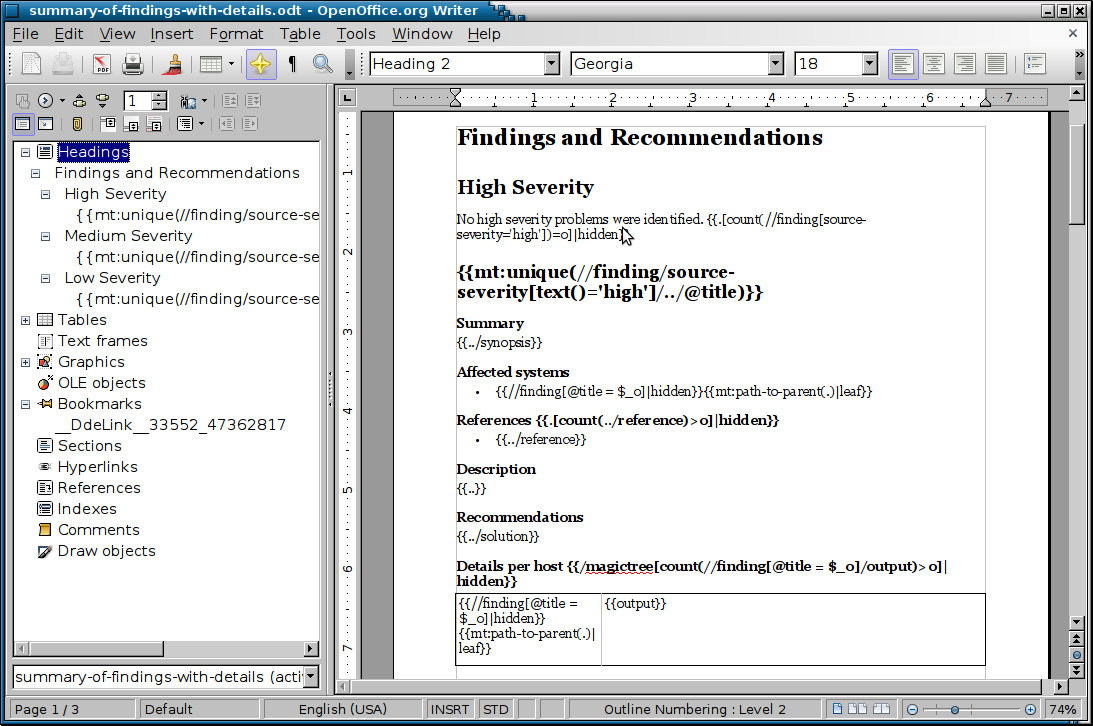
Generated Report
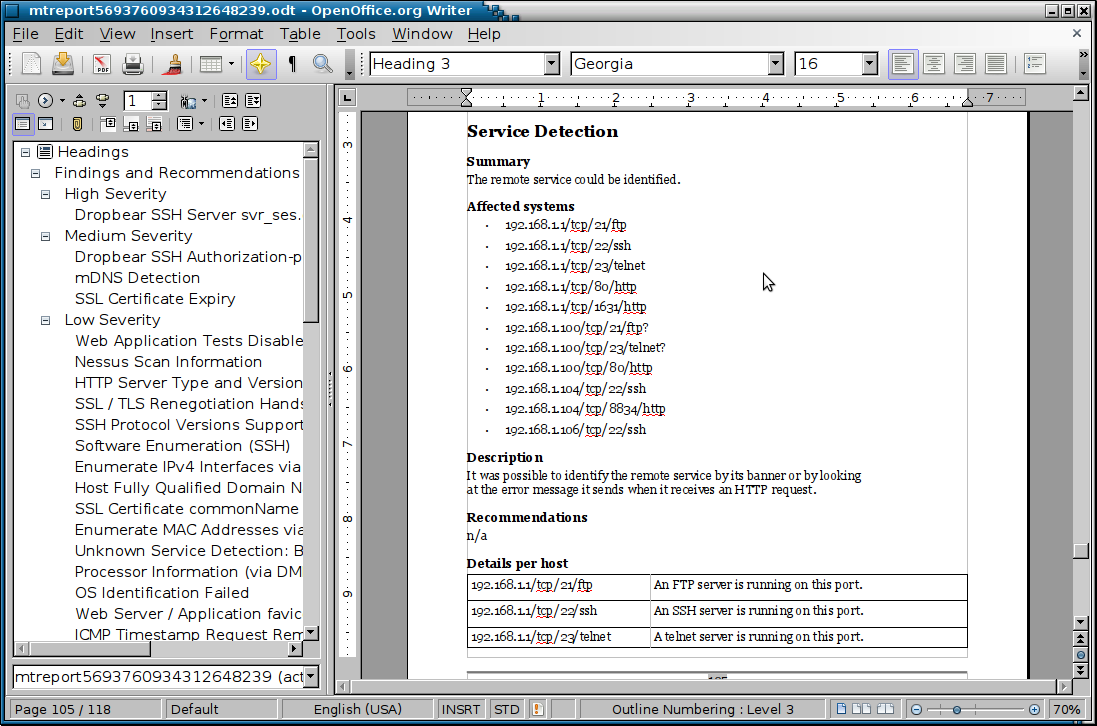
Using magictree
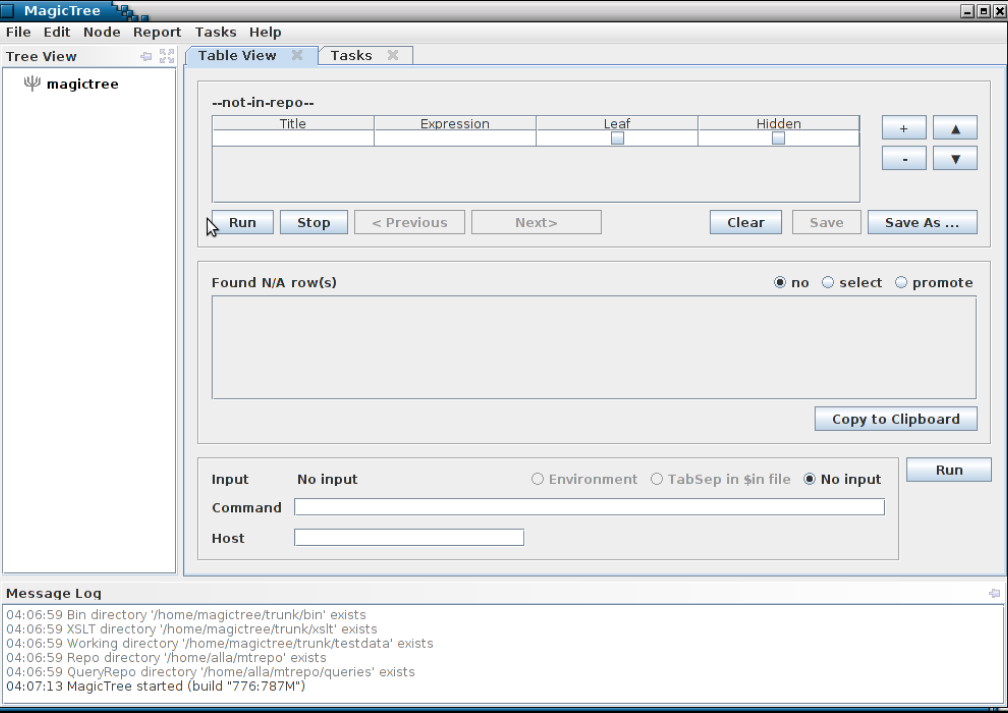
Step 1
You start with an empty tree:
Step 2
You begin by adding some data to the tree. For example, you add some networks and hosts that are in scope of the test.
MagicTree stores data in a tree structure. This is a natural way for representing the information that is gathered during a network test: a host has ports, which have services, applications, vulnerabilities, etc. The tree like structure is also flexible in terms of adding new information without disturbing the existing data structure: if you at some point decide that you need the MAC address of the host, you just add another child node to the host node.
While tree structure is natural for representing the information, it is not very convenient for actually using the data. To feed data to programs we generally want lists or tables of items. MagicTree allows extracting the data and presenting it in table (or list) form. The query interface uses XPath expressions to extract data.
Step 3
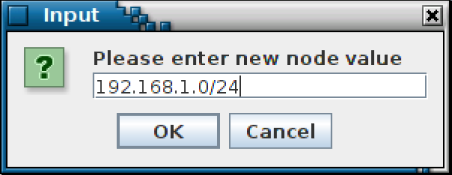
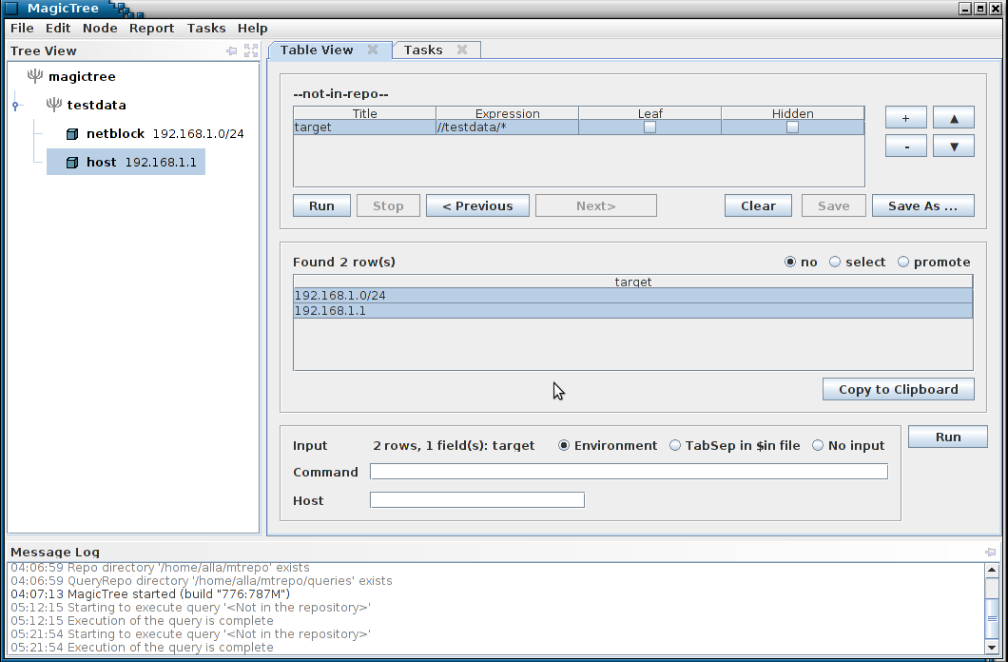
So, suppose now we want to run a ping sweep on all targets in scope. First we select them, using a query:
Step 4
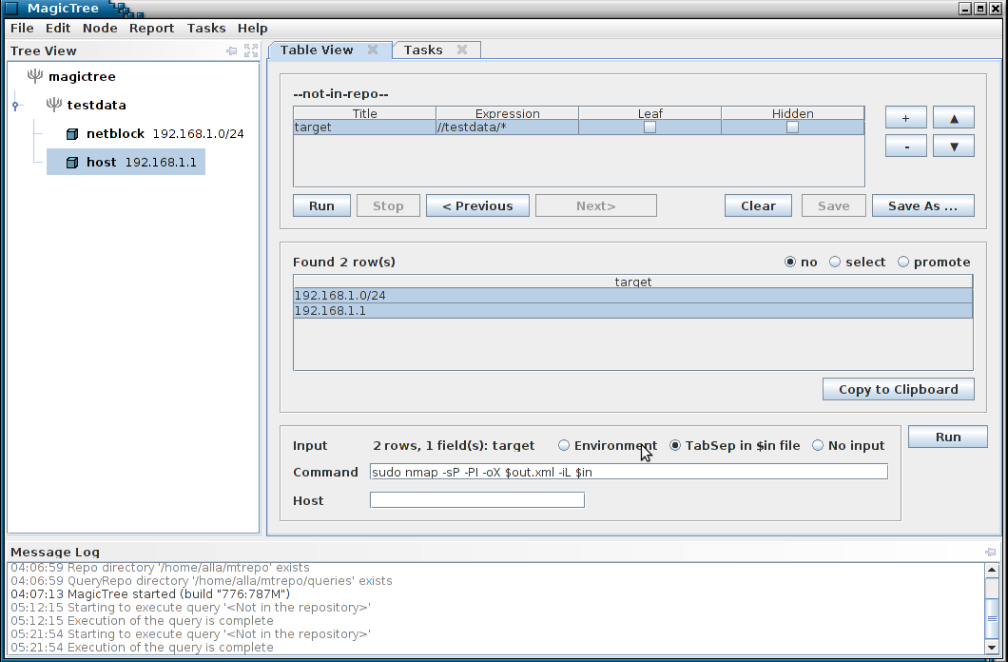
The data we want is now in the table, so we can feed it to nmap.
Note the $in parameter in nmap command line. It is a temporary file containing tab separated query results. The nmap XML output goes to $out.xml . $out is a special prefix which tells MagicTree that it contains some command output. Clicking "Run" will start nmap.
Step 5
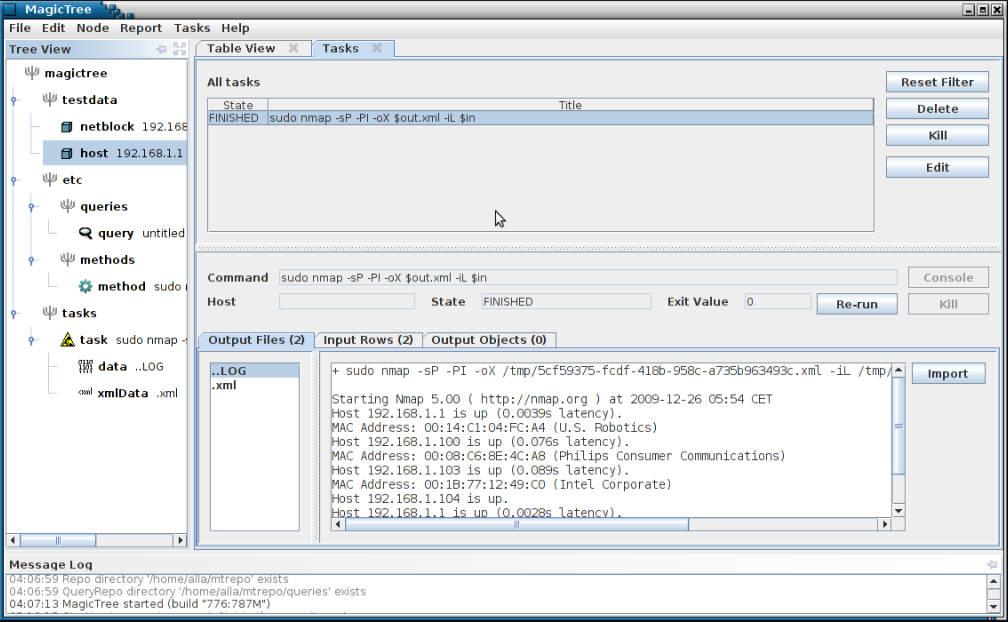
You can start multiple commands in parallel. You can run things locally and remotely (on remote hosts that have SSH daemon and a Unix-like shell). You see all running and finished commands in Task Manager.
Step 6
The command has produced both human-readable output and an XML file. We can import XML data into the tree. The newly added tree nodes are shown in green in the tree.
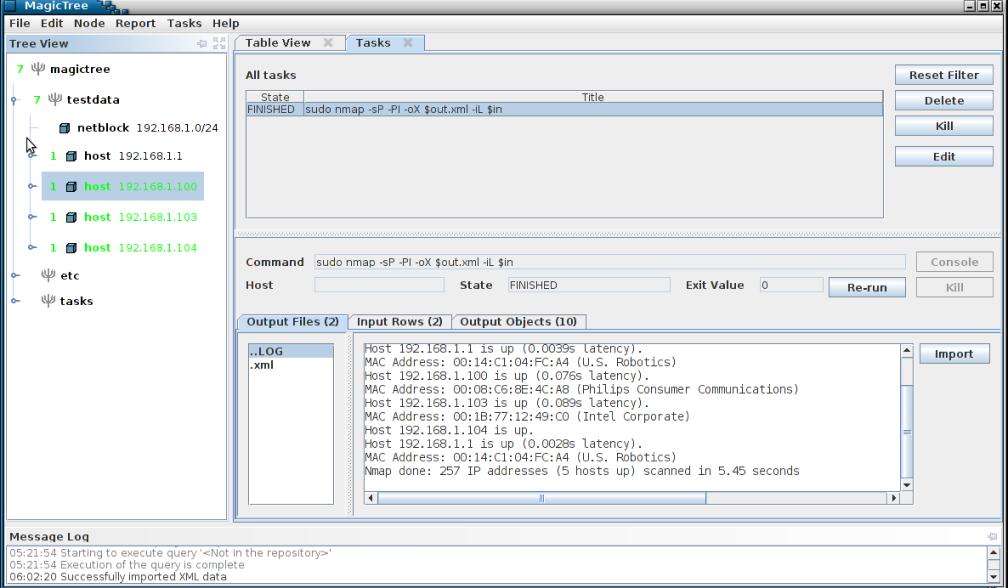
Step 7
Now let's run a TCP port scan for all discovered hosts. We will run a query that selects hosts with state "up" and again feed the data to nmap. We will then import the new data in the tree as we did before. At any time you can access the console to any running task - local or remote.
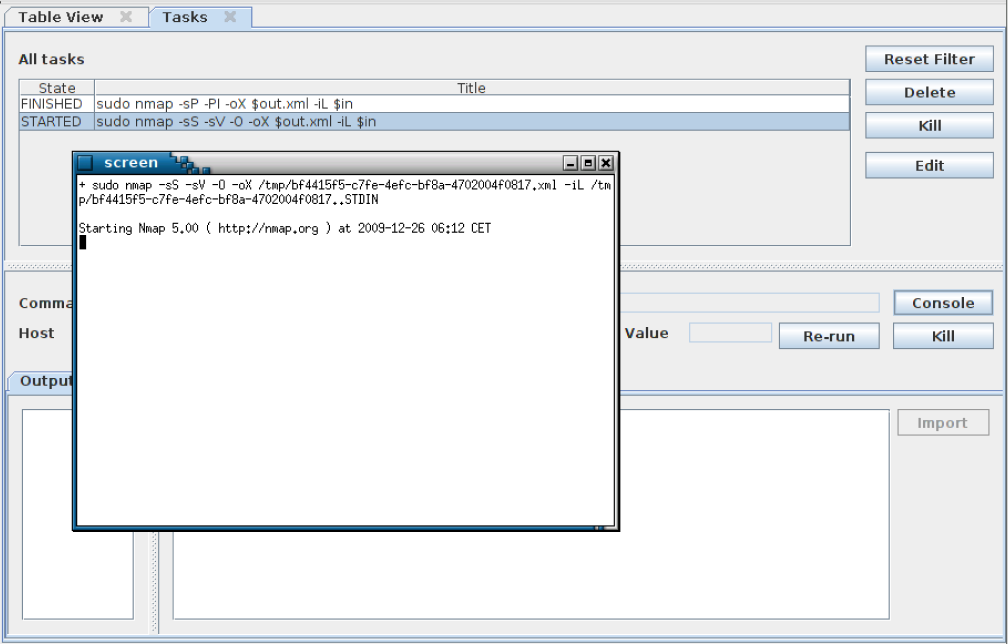
Step 8
We can continue querying the data and feeding it to various tools. The query shown on the screenshot below lists all open ports and hosts.
For tools that do not produce XML, the text output is still retained and can be viewed and included in reports, but can not be directly imported into the tree. We are developing wrappers for commonly used tools to convert text output to XML. The tree can contain text, images, XML documents, and even arbitrary binary data. We also support cross-references within a tree, so that one node can refer to another. This is convenient when you need to link a finding to affected hosts, and so on.
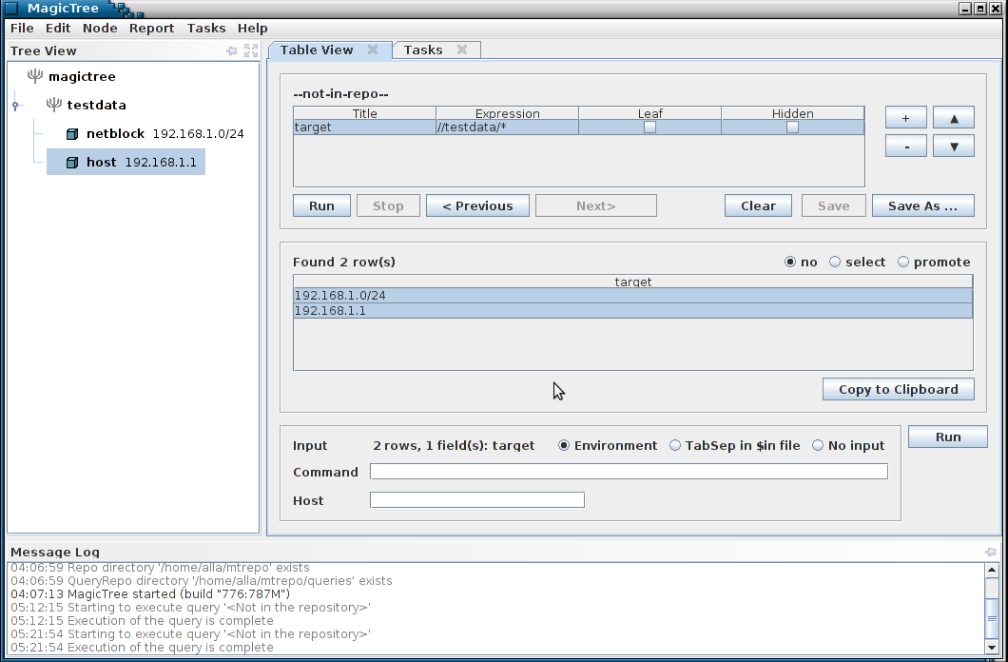
Step 9
Once you have all the data you want, you can use it to produce a report. Reports are generated from templates. A template is simply an OpenOffice or Microsoft Word file that contains all the static data and formatting you want (your company logos, headers, footers, etc.) and placeholders for the data coming from MagicTree. The placeholders are XPath expressions, similar to ones used in a query. Here is an template snippet that produces a host section:

Note that you can have automatically generated hyperlinks in your report, so you link to detailed results from a summary, to command output from host details and so on.
Several sample report templates come with MagicTree. You can modify and customize them to your liking.
Imagine, after spending a few days testing, just clicking on "Generate Report" and having all (or the important part) of your test data in a human readable report. No more mind-numbing copy-pasting. Unbelievable, right? You have to try it.
Contacts

+32 (0) 2 215 53 58

Gremwell BVBA
Sint-Katherinastraat 24
1742 Ternat
Belgium
VAT: BE 0821.897.133.

